Access IoT SSH AWS: The Ultimate Guide To Secure Remote Connections
Hey there, tech enthusiasts! If you're reading this, chances are you're diving headfirst into the world of cloud computing and IoT (Internet of Things). Let’s face it—managing devices remotely has become a necessity in today’s hyper-connected world. And when it comes to secure remote access, access IoT SSH AWS is a game-changer. But what exactly does that mean? Well, buckle up because we're about to break it down for you in a way that’s easy to digest and super actionable.
Think of SSH (Secure Shell) as the digital bouncer at a fancy club. It ensures only authorized users get in while keeping the bad guys out. Now, when you combine SSH with AWS (Amazon Web Services) and IoT, you’ve got yourself a powerful trifecta that can revolutionize how you manage your devices. Whether you're a seasoned pro or just starting out, this guide is packed with insights and practical tips to help you master the art of secure remote access.
By the end of this article, you’ll not only understand the basics but also learn advanced techniques to set up and maintain secure connections. So grab your favorite beverage, sit back, and let’s dive into the world of IoT SSH on AWS!
Read also:Discover The World Of Divaflawless Onlyfans Videos A Deep Dive
Table of Contents
- What is SSH and Why It Matters
- AWS IoT Overview: The Backbone of Connectivity
- Setting Up SSH for IoT Devices
- Security Best Practices for SSH on AWS
- Common Issues and How to Fix Them
- Tools You Need to Access IoT SSH AWS
- Real-World Use Cases of IoT SSH on AWS
- Performance Tips for SSH Connections
- Future Trends in IoT SSH AWS
- Wrapping It Up: Your Next Steps
What is SSH and Why It Matters
Alright, let’s start with the basics. SSH stands for Secure Shell, and it’s basically a protocol that allows you to securely connect to remote devices over an unsecured network. Think of it as a secret handshake that ensures you’re talking to the right device and vice versa.
Why does SSH matter in the context of IoT SSH AWS? Well, IoT devices are everywhere these days—smart home gadgets, industrial sensors, wearable tech, you name it. And while these devices make our lives easier, they also introduce new security risks. SSH helps mitigate those risks by encrypting your communications and verifying the identity of both parties involved.
Now, here’s the kicker: when you’re dealing with AWS, you’ve got access to a whole suite of tools and services that make managing SSH connections a breeze. From EC2 instances to IoT Core, AWS has got you covered. But more on that later!
Key Features of SSH
- Encryption: Protects your data from prying eyes.
- Authentication: Ensures only authorized users can access your devices.
- Flexibility: Works across a wide range of devices and operating systems.
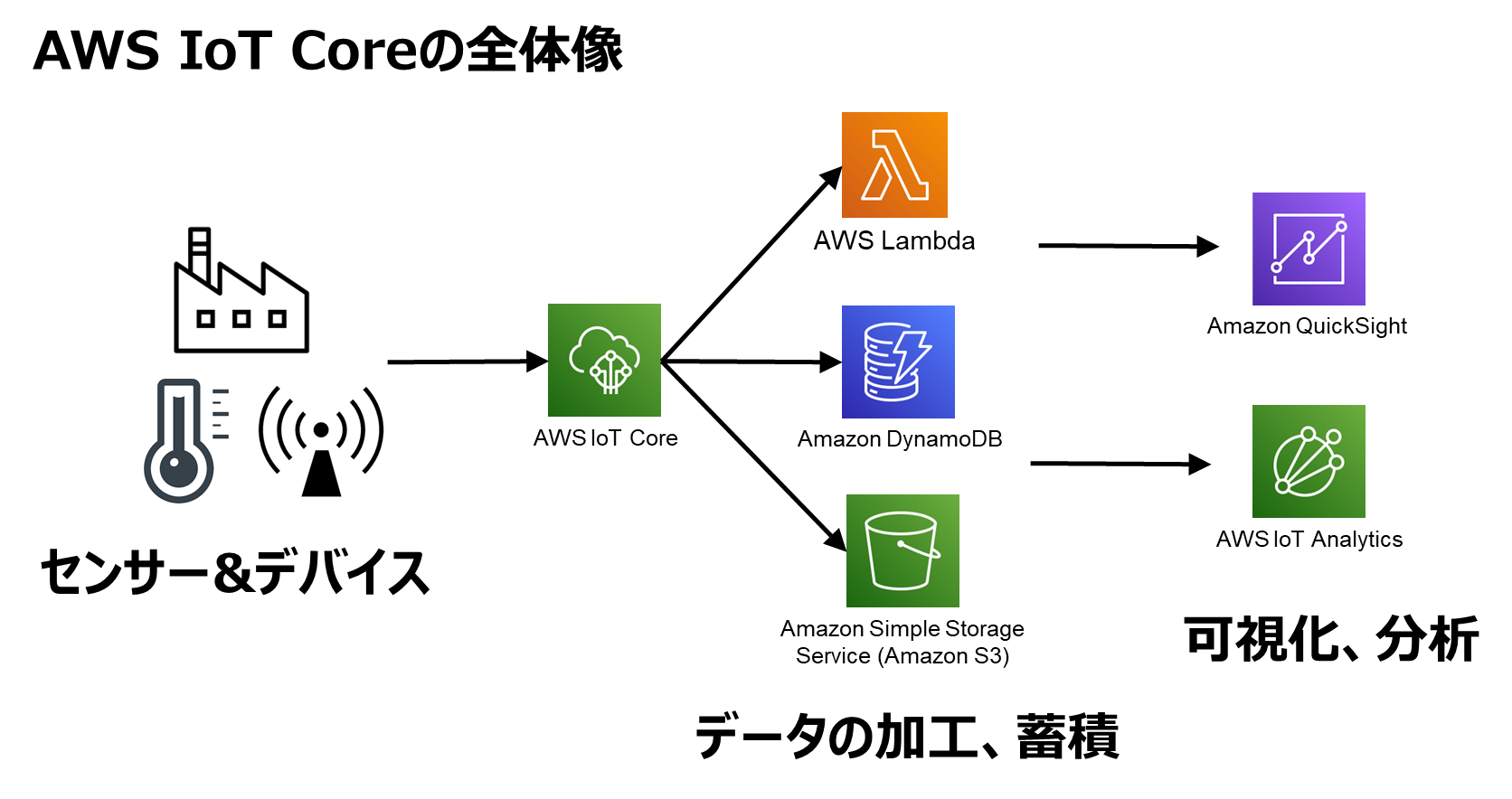
AWS IoT Overview: The Backbone of Connectivity
Let’s talk about AWS IoT for a moment. AWS IoT is like the nervous system of your connected devices. It allows you to securely interact with billions of devices and manage their data in real-time. Whether you’re building a smart city or automating your home, AWS IoT provides the infrastructure you need to make it happen.
But how does it tie into access IoT SSH AWS? Simple. AWS IoT Core, one of the key services in the AWS IoT suite, allows you to connect devices to the cloud and manage them using protocols like MQTT, HTTP, and—you guessed it—SSH. This means you can remotely configure, monitor, and troubleshoot your devices without ever having to physically touch them.
Benefits of Using AWS IoT
- Scalability: Easily scale your operations as your device fleet grows.
- Security: AWS provides robust security features to protect your devices and data.
- Integration: Seamlessly integrate with other AWS services for a comprehensive solution.
Setting Up SSH for IoT Devices
So, you’ve got your IoT devices and you’re ready to set up SSH. Where do you start? First things first, you’ll need to ensure your devices are properly configured to accept SSH connections. This typically involves setting up a public/private key pair and configuring your firewall rules.
Read also:Hdhub4u Home Your Ultimate Destination For Highquality Entertainment
Here’s a step-by-step guide to help you get started:
- Generate an SSH key pair using a tool like
ssh-keygen. - Upload the public key to your IoT device.
- Configure your device to allow SSH connections on the desired port (usually 22).
- Set up firewall rules to restrict access to trusted IP addresses.
Once you’ve completed these steps, you should be able to connect to your device using an SSH client like PuTTY or OpenSSH.
Common Mistakes to Avoid
- Using weak passwords instead of key-based authentication.
- Leaving default ports open to the public internet.
- Not regularly updating your device firmware and SSH software.
Security Best Practices for SSH on AWS
Security is paramount when it comes to IoT SSH AWS. After all, you’re dealing with sensitive data and potentially mission-critical systems. Here are some best practices to keep your connections secure:
First and foremost, always use key-based authentication instead of passwords. This eliminates the risk of brute-force attacks and ensures only authorized users can access your devices. Additionally, consider using a bastion host to limit direct access to your devices from the internet.
Another crucial step is to regularly update your SSH software and device firmware. This ensures you’re protected against the latest vulnerabilities and exploits. And don’t forget to monitor your logs for any suspicious activity. AWS CloudWatch can be a great tool for this, providing real-time insights into your system’s behavior.
Advanced Security Tips
- Use multi-factor authentication (MFA) for added security.
- Implement network segmentation to isolate critical devices.
- Regularly audit your security settings and adjust as needed.
Common Issues and How to Fix Them
Even the best-laid plans can go awry sometimes. Here are some common issues you might encounter when working with IoT SSH AWS and how to fix them:
One common problem is connection timeouts. This can happen for a variety of reasons, such as network congestion or misconfigured firewall rules. To troubleshoot, try increasing the timeout value in your SSH client or double-checking your firewall settings.
Another issue is authentication failures. If you’re unable to log in, make sure your public key is correctly installed on the device and that your private key is properly secured. Also, verify that your username matches the one configured on the device.
Troubleshooting Checklist
- Check your SSH client settings.
- Verify your public/private key pair.
- Inspect your firewall rules and network configuration.
Tools You Need to Access IoT SSH AWS
Now that you’ve got the basics down, let’s talk about the tools you’ll need to make the most of IoT SSH AWS. First and foremost, you’ll need an SSH client. PuTTY is a popular choice for Windows users, while OpenSSH is built into most Linux and macOS systems.
For managing your AWS resources, the AWS Management Console and AWS CLI (Command Line Interface) are indispensable. These tools allow you to configure your IoT devices, manage your SSH keys, and monitor your system’s performance.
And don’t forget about third-party tools like Terraform and Ansible, which can help automate your workflows and streamline your operations. With the right tools in your arsenal, managing IoT SSH AWS becomes a breeze.
Real-World Use Cases of IoT SSH on AWS
Enough theory—let’s look at some real-world examples of how IoT SSH AWS is being used today. One common use case is remote monitoring and maintenance of industrial equipment. By connecting machines to the cloud and using SSH for secure access, companies can reduce downtime and improve efficiency.
Another exciting application is in the smart home space. Devices like thermostats, security cameras, and lighting systems can all be managed remotely using SSH, giving homeowners unprecedented control over their living environments.
And let’s not forget about the healthcare industry. IoT-enabled medical devices are revolutionizing patient care, and SSH ensures that sensitive patient data remains secure and compliant with regulations like HIPAA.
Industries Using IoT SSH AWS
- Manufacturing
- Healthcare
- Smart Cities
- Energy and Utilities
Performance Tips for SSH Connections
Speed and reliability are key when it comes to IoT SSH AWS. Here are some tips to help you optimize your connections:
First, consider using compression to reduce the amount of data transmitted over the network. This can significantly improve performance, especially on slow or unreliable connections. Additionally, you can tweak your SSH configuration to use faster encryption algorithms like AES-128.
Another trick is to enable keepalive packets. This helps maintain your connection even if there’s a temporary network disruption. Just be sure to set the interval appropriately to avoid overwhelming your device.
Optimization Techniques
- Enable compression for faster data transfer.
- Use faster encryption algorithms like AES-128.
- Set keepalive intervals to maintain stable connections.
Future Trends in IoT SSH AWS
Looking ahead, the future of IoT SSH AWS is bright. As more devices come online, the demand for secure and efficient remote access solutions will only continue to grow. Expect to see advancements in areas like quantum-resistant cryptography and machine learning-based threat detection.
Another trend to watch is the rise of edge computing. By processing data closer to the source, edge devices can reduce latency and improve performance. AWS is already investing heavily in this space, with services like AWS IoT Greengrass enabling local computation and communication between devices.
And let’s not forget about the growing importance of sustainability. As companies strive to reduce their carbon footprint, efficient resource management will become increasingly critical. SSH and other remote access technologies will play a key role in achieving this goal.
Wrapping It Up: Your Next Steps
There you have it—a comprehensive guide to access IoT SSH AWS. From understanding the basics to mastering advanced techniques, you now have the knowledge and tools you need to take your IoT deployments to the next level.
But remember, this is just the beginning. The world of IoT and cloud computing is constantly evolving, so it’s important to stay informed and adapt to new technologies as they emerge. Be sure to check out the official AWS documentation and join online communities to stay up-to-date with the latest trends and best practices.
And finally, don’t forget to share your newfound expertise with others. Whether it’s through blog posts, social media, or in-person conversations, spreading knowledge benefits us all. So go ahead, make an impact, and let’s build a smarter, more connected world together!