Is VNC A Security Risk? Unveiling The Truth Behind Remote Access Technology
Ever wondered if VNC is a security risk? Let’s dive into the world of remote desktop solutions and uncover what’s really going on behind the scenes. VNC, or Virtual Network Computing, has been around for years, but with the rise of cyber threats, people are starting to question its safety. Is it really as secure as we think, or are we opening ourselves up to potential breaches?
VNC is a powerful tool that allows users to access and control remote computers from anywhere in the world. Sounds great, right? But here’s the catch – with great power comes great responsibility. If not configured properly, VNC can become a gateway for hackers to infiltrate your system. So, before you jump into using VNC, let’s break it down and explore whether it’s truly a security risk or just a misunderstood technology.
In this article, we’ll delve deep into the ins and outs of VNC, discussing its security features, potential vulnerabilities, and how you can protect yourself. Whether you’re a tech enthusiast, a business owner, or simply someone looking to stay safe online, this guide will give you all the information you need to make an informed decision. Let’s get started!
Read also:Hshub4u Your Ultimate Guide To The World Of Digital Solutions And Beyond
Here’s a quick breakdown of what we’ll cover:
- What is VNC?
- VNC Security Features
- Common VNC Security Risks
- How to Secure VNC
- VNC Alternatives
- VNC for Business
What is VNC?
VNC, or Virtual Network Computing, is a remote desktop technology that allows you to access and control another computer over the internet. Think of it as a digital bridge that connects two devices, enabling you to operate one computer from another, no matter where you are. This tool is widely used by IT professionals, remote workers, and even everyday users who need to troubleshoot issues or access files on a distant machine.
At its core, VNC works by transmitting the screen of the remote computer to your local device in real-time. You can then interact with the remote system as if you were sitting right in front of it. It’s like having a virtual clone of your computer, but with the added convenience of being able to access it from anywhere. Sounds awesome, right? But hold up – is it safe?
How Does VNC Work?
VNC operates on a client-server model. The remote computer acts as the server, while your local device serves as the client. When you connect to the remote machine, VNC sends updates of the screen and input commands (like keyboard and mouse actions) between the two devices. This process happens almost instantaneously, allowing for seamless interaction.
However, the way VNC transmits data can sometimes leave it vulnerable to attacks if not properly secured. That’s why understanding how it works is crucial in mitigating potential risks. Let’s move on to the next section to explore the security features of VNC.
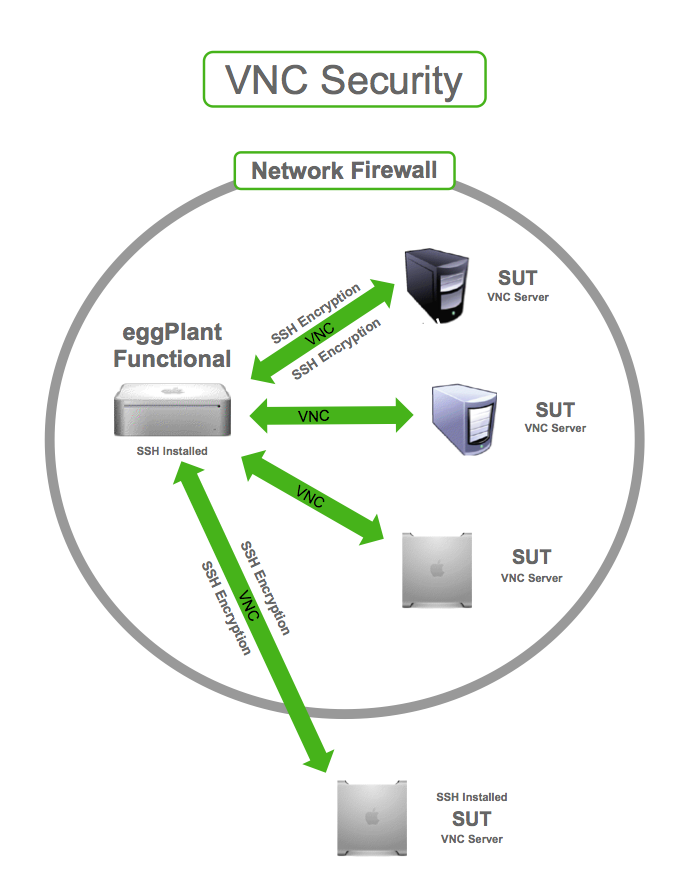
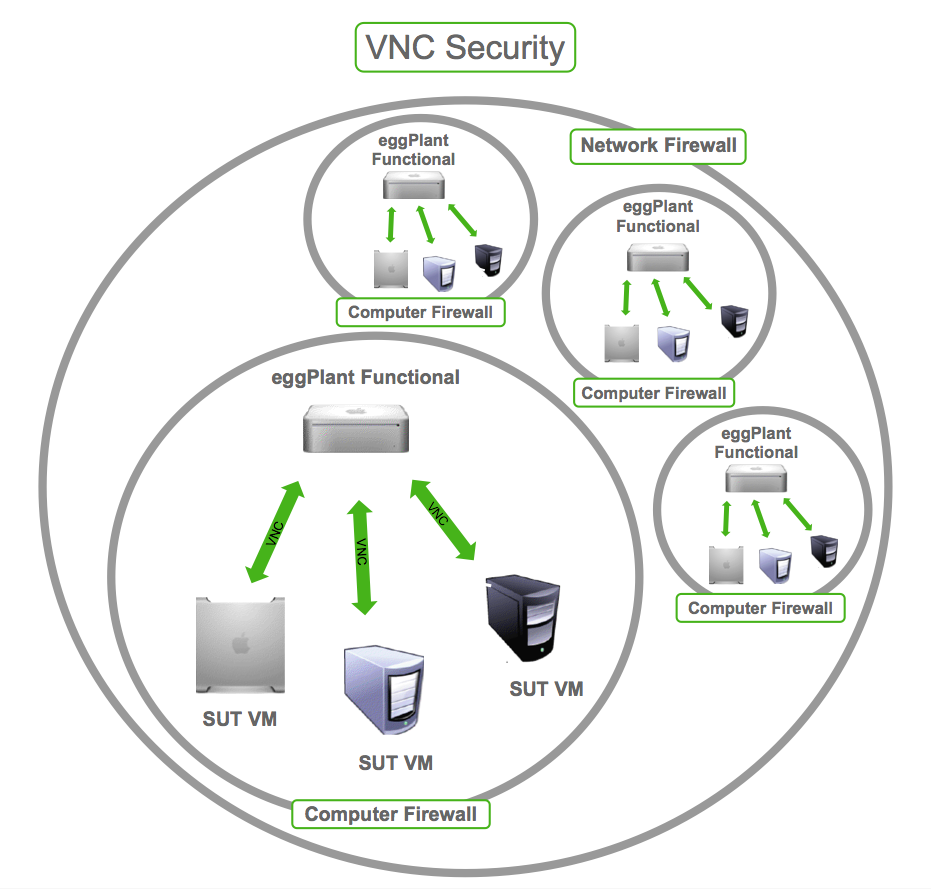
VNC Security Features
Now that we know what VNC is and how it works, let’s talk about its security features. VNC wasn’t originally designed with security in mind, but over the years, developers have added various layers of protection to make it safer. Here are some of the key security features you should be aware of:
Read also:Divaflawless Sex Unveiling The Truth Behind The Online Persona
- Encryption: Modern VNC implementations offer encryption for data transmitted between the client and server. This ensures that sensitive information, like passwords and files, is protected from prying eyes.
- Authentication: VNC requires users to enter a password before gaining access to the remote system. This helps prevent unauthorized access and ensures only authorized individuals can connect.
- Firewall Integration: Many VNC clients can be configured to work behind firewalls, adding an extra layer of security to your connection.
- Access Control: Some VNC solutions allow you to set permissions for different users, limiting what they can and cannot do on the remote machine.
While these features provide a good foundation for security, they’re only as effective as how you implement them. Let’s take a closer look at the potential risks associated with VNC in the next section.
Common VNC Security Risks
Even with all the security features in place, VNC isn’t completely immune to risks. Here are some of the most common security threats associated with VNC:
1. Weak Passwords
One of the biggest culprits of VNC-related security breaches is weak passwords. If you’re using a simple, easily guessable password, you’re practically inviting hackers to break into your system. Always use strong, unique passwords that combine letters, numbers, and symbols.
2. Lack of Encryption
Not all VNC implementations come with encryption enabled by default. If you’re using an older version or a less secure client, your data could be transmitted in plain text, making it easy for attackers to intercept sensitive information.
3. Unsecured Networks
Connecting to VNC over unsecured networks, like public Wi-Fi, can expose your connection to eavesdropping and man-in-the-middle attacks. Always use a secure network or a Virtual Private Network (VPN) when accessing VNC.
4. Misconfigured Settings
Improperly configured VNC settings can leave your system wide open to attacks. For example, failing to restrict access to specific IP addresses or not enabling encryption can create vulnerabilities that hackers can exploit.
Now that we’ve identified the risks, let’s talk about how you can secure your VNC connection.
How to Secure VNC
Securing your VNC connection doesn’t have to be complicated. Here are some simple yet effective steps you can take to protect yourself:
- Use Strong Passwords: As we mentioned earlier, weak passwords are a major security risk. Make sure to use strong, unique passwords for your VNC connections.
- Enable Encryption: Always enable encryption when setting up your VNC client. This will ensure that your data is transmitted securely.
- Restrict Access: Limit access to your VNC server by specifying which IP addresses are allowed to connect. This reduces the risk of unauthorized access.
- Use a Firewall: Configure your firewall to block unauthorized access to your VNC port. This adds an extra layer of protection to your system.
- Keep Software Updated: Regularly update your VNC client and server software to ensure you have the latest security patches and features.
By following these steps, you can significantly reduce the risk of a security breach and enjoy a safer VNC experience. Let’s now explore some alternatives to VNC.
VNC Alternatives
If you’re still not convinced that VNC is the right choice for you, there are plenty of alternatives to consider. Here are some popular options:
1. TeamViewer
TeamViewer is a widely used remote desktop solution that offers robust security features, including end-to-end encryption and multi-factor authentication. It’s easy to set up and use, making it a great choice for both personal and business use.
2. AnyDesk
AnyDesk is another popular alternative to VNC. It boasts high-speed connections and strong encryption, ensuring a secure and reliable remote desktop experience. Plus, it’s available on multiple platforms, including Windows, macOS, Linux, and mobile devices.
3. Remote Desktop Protocol (RDP)
RDP is a built-in remote desktop solution for Windows users. While it doesn’t offer the same level of flexibility as VNC, it’s a secure and reliable option for accessing Windows-based systems remotely.
Choosing the right alternative depends on your specific needs and preferences. Make sure to do your research and select a solution that best fits your requirements.
VNC for Business
For businesses, VNC can be a valuable tool for remote work, IT support, and collaboration. However, it’s important to implement proper security measures to protect sensitive company data. Here are some tips for using VNC in a business environment:
1. Create a Security Policy
Establish a clear security policy for VNC usage within your organization. This should include guidelines for password management, encryption, and access control.
2. Train Your Employees
Make sure your employees are aware of the potential risks associated with VNC and how to use it safely. Regular training sessions can help reinforce best practices and keep everyone informed.
3. Monitor Usage
Keep an eye on VNC usage within your organization to detect any suspicious activity. Implement logging and monitoring tools to track who’s accessing what and when.
By following these tips, businesses can safely harness the power of VNC to improve productivity and collaboration.
Kesimpulan
In conclusion, VNC can be a secure and reliable tool for remote access if used properly. While there are potential risks associated with VNC, they can be mitigated by implementing strong security measures and following best practices. Whether you’re using VNC for personal or business purposes, always prioritize security to protect yourself and your data.
We encourage you to leave a comment below sharing your thoughts on VNC and its security risks. Have you encountered any issues with VNC in the past? How do you ensure your remote connections are secure? Let’s start a conversation and help each other stay safe online!