VNC Security Risk Issues: Are You Exposing Your Network?
Hey there, tech-savvy friend! If you're diving into the world of remote desktop tools, chances are you've come across VNC. It's like the Swiss Army knife of remote access solutions, but hold up—there's a catch. VNC security risk issues are real, and they could be putting your system in jeopardy. Ever wondered how secure your VNC setup really is? Stick around because we’re about to deep-dive into this topic like it's an episode of CSI: Cyber.
VNC (Virtual Network Computing) is one of those tools that’s been around for ages, and for good reason. It lets you control another computer from afar, which is super handy for IT pros, remote workers, and anyone who needs to troubleshoot systems without being physically present. But let’s not kid ourselves—VNC isn’t without its flaws. Security risks are lurking in the shadows, and if you’re not careful, they can bite you where it hurts.
Now, I’m not here to scare you into uninstalling VNC altogether. What I want to do is arm you with knowledge so you can make informed decisions. By the end of this article, you’ll know exactly what VNC security risks to look out for, how to mitigate them, and why protecting your network is non-negotiable. So, buckle up and let’s get started!
Read also:5movierulz Kannada 2025 Your Ultimate Guide To Latest Movies And Downloads
What Exactly is VNC and Why Should You Care?
VNC, or Virtual Network Computing, is like the OG of remote desktop tools. It’s been around since the late '90s and has become a staple in many IT departments. Essentially, VNC allows you to control another computer remotely, as if you were sitting right in front of it. Cool, right? But here’s the kicker: VNC wasn’t originally designed with security in mind. Back in the day, people weren’t as paranoid about hackers and cybercriminals as they are now. Fast forward to today, and we’re dealing with a tool that’s powerful but potentially dangerous if misconfigured.
How VNC Works: Breaking It Down
VNC operates on a client-server model. The server is the machine you want to control, and the client is the device you’re using to access it. When you connect to a VNC server, you get a live feed of the server’s screen, and you can interact with it just like you would if you were physically there. Sounds great, but here’s where things can go south:
- Unencrypted Connections: By default, older versions of VNC don’t encrypt data, meaning your keystrokes, mouse movements, and even sensitive information could be intercepted by malicious actors.
- Weak Passwords: If you’re using a weak or default password, you’re practically rolling out the red carpet for hackers.
- Public Exposure: If your VNC server is exposed to the internet without proper security measures, it’s like leaving your house unlocked with a neon sign that says, “Hack me!”
Top VNC Security Risk Issues You Need to Know
Alright, let’s get real for a second. VNC security risk issues aren’t just theoretical—they’re happening out there in the wild. Here’s a breakdown of the most common problems you might face:
1. Lack of Encryption
Encryption is like the bouncer at a club—it keeps the bad guys out. Unfortunately, many VNC implementations don’t use encryption by default. This means that all your data, including passwords and sensitive files, could be transmitted in plain text. Think about it: would you send your bank details over email without encryption? Probably not. So why would you do it with VNC?
2. Default Credentials
Another big no-no is using default credentials. Many VNC servers come with pre-set usernames and passwords that are well-known in the hacker community. If you don’t change these defaults, you’re basically inviting attackers to waltz right in.
3. Publicly Exposed Servers
Exposing your VNC server to the public internet without proper security measures is a recipe for disaster. Cybercriminals use automated tools to scan for open VNC ports, and once they find one, they’ll try to brute-force their way in. If they succeed, they can take full control of your system.
Read also:Divine Discoveries Your Ultimate Guide To Diva Flawless Onlyfans Free Content
Why VNC Security Matters: Real-Life Examples
You might be thinking, “Okay, but does this stuff really happen?” The answer is a resounding yes. Let me give you a couple of real-life examples to illustrate the dangers of neglecting VNC security:
Case Study 1: The Mass VNC Breach
In 2018, researchers discovered over 700,000 VNC servers exposed to the internet. Many of these servers were using default credentials or weak passwords, making them easy targets for hackers. The attackers didn’t even need to try very hard—they simply scanned for open VNC ports and brute-forced their way in. The result? Hundreds of thousands of systems compromised, with potentially disastrous consequences for the organizations involved.
Case Study 2: Ransomware via VNC
Ransomware is a growing threat, and VNC is one of the vectors attackers use to deploy it. In one notable incident, hackers gained access to a company’s network through an unsecured VNC server. Once inside, they deployed ransomware that encrypted critical files and demanded a hefty ransom for their release. The company ended up paying the ransom, but the damage was already done—lost data, reputational harm, and financial losses.
How to Secure Your VNC Setup
Now that you know the risks, let’s talk about how to protect yourself. Securing your VNC setup doesn’t have to be complicated, but it does require some attention to detail. Here are a few tips to get you started:
1. Enable Encryption
Encryption is your first line of defense. Make sure your VNC client and server support encryption, and enable it whenever possible. This will help protect your data from prying eyes.
2. Use Strong Passwords
Weak passwords are like leaving your front door unlocked. Use strong, unique passwords for your VNC server, and consider enabling two-factor authentication (2FA) for an extra layer of security.
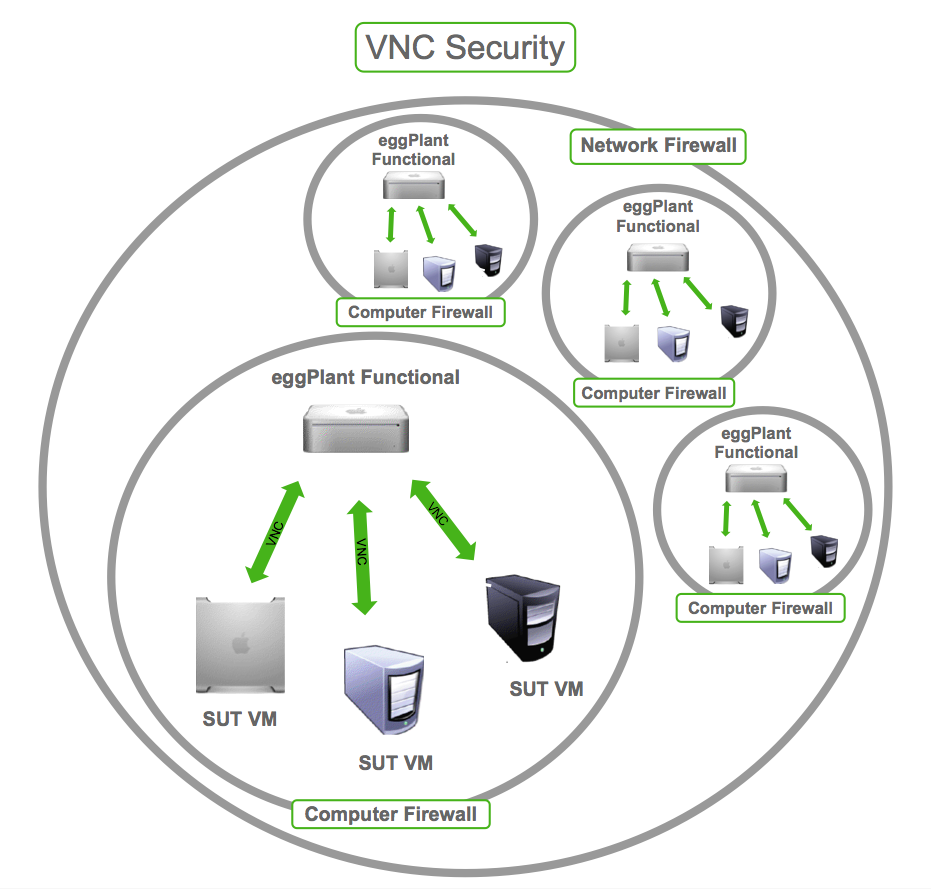
3. Restrict Access
Don’t expose your VNC server to the public internet unless absolutely necessary. If you must expose it, use a firewall to restrict access to trusted IP addresses only. This will significantly reduce the risk of unauthorized access.
Advanced VNC Security Tips
If you’re looking to take your VNC security to the next level, here are a few advanced tips to consider:
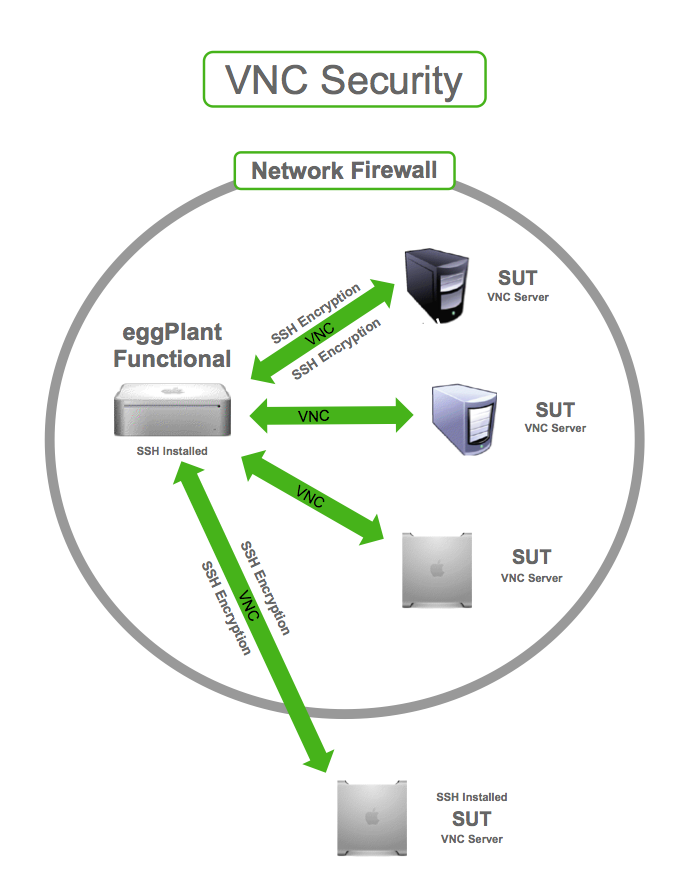
1. Use SSH Tunneling
SSH tunneling is a technique that encrypts your VNC connection by routing it through an SSH session. This adds an extra layer of security and makes it much harder for attackers to intercept your data.
2. Regularly Update Your Software
Software updates often include security patches that fix known vulnerabilities. Keep your VNC client and server software up to date to ensure you’re protected against the latest threats.
3. Monitor for Suspicious Activity
Set up monitoring tools to alert you to any suspicious activity on your VNC server. This could include failed login attempts, unusual connection patterns, or unauthorized access attempts.
VNC Security Best Practices: A Quick Checklist
Here’s a quick checklist to help you secure your VNC setup:
- Enable encryption for all VNC connections.
- Use strong, unique passwords and enable 2FA if possible.
- Restrict access to trusted IP addresses using a firewall.
- Use SSH tunneling for added security.
- Keep your VNC software updated with the latest security patches.
- Monitor for suspicious activity and investigate any potential threats.
Common Misconceptions About VNC Security
There are a few common misconceptions about VNC security that I want to clear up:
1. “VNC is Secure Enough for My Needs”
While VNC is a powerful tool, it’s not inherently secure. If you don’t take the necessary precautions, you’re putting your system at risk.
2. “I Don’t Need to Worry About Encryption”
Encryption might seem like overkill, but it’s essential for protecting your data. Without it, your VNC sessions are vulnerable to interception and eavesdropping.
3. “Hackers Won’t Target Me”
Think again. Cybercriminals use automated tools to scan for vulnerable systems, and they don’t discriminate. If your VNC server is exposed to the internet, you’re a potential target.
The Future of VNC Security
As technology evolves, so do the threats we face. The good news is that VNC developers are constantly working to improve security. New versions of VNC include features like stronger encryption, better authentication mechanisms, and more robust security protocols. However, it’s up to us as users to take advantage of these features and implement them correctly.
What Can We Expect in the Future?
In the future, we can expect to see even more advanced security features in VNC, such as AI-driven threat detection, biometric authentication, and seamless integration with other security tools. These advancements will help make VNC a safer and more secure option for remote access.
Conclusion: Protect Your VNC Setup Today
So there you have it—a comprehensive look at VNC security risk issues and how to address them. VNC is a powerful tool, but it’s not without its flaws. By understanding the risks and taking the necessary precautions, you can protect your system and avoid becoming another statistic in the world of cybercrime.
Before I go, I want to leave you with a call to action. Take a few minutes today to review your VNC setup and make sure it’s as secure as possible. Enable encryption, use strong passwords, and restrict access to trusted users only. And if you’re not sure where to start, feel free to reach out in the comments below. I’d be happy to help!
Thanks for reading, and stay safe out there!
Table of Contents
- What Exactly is VNC and Why Should You Care?
- Top VNC Security Risk Issues You Need to Know
- Why VNC Security Matters: Real-Life Examples
- How to Secure Your VNC Setup
- Advanced VNC Security Tips
- VNC Security Best Practices: A Quick Checklist
- Common Misconceptions About VNC Security
- The Future of VNC Security
- Conclusion: Protect Your VNC Setup Today
![[2025] Fixed! VNC's "Too Many Security Failures" Error](https://images.airdroid.com/2024/09/how-to-fix-vnc-too-many-security-failures-02-768x548.png)