VNC Security Risks: How Safe Is Your Remote Connection?
Hey there, tech-savvy friend! Let me ask you something—how often do you use Virtual Network Computing (VNC) for remote access? If you're like most people, probably more than you think. But here's the deal: while VNC is super convenient, it also comes with a heap of security risks you might not even realize. VNC security risks are real, and they can hit hard if you’re not careful. So, buckle up because we’re about to dive deep into the world of remote connections and uncover the hidden dangers lurking in the shadows.
You see, VNC allows you to control a computer from afar, which is awesome for remote work, troubleshooting, or managing servers. But just like leaving your front door unlocked, using VNC without proper security measures is basically inviting trouble. In this article, we’ll break down the risks, show you how to protect yourself, and share some insider tips to keep your data safe. Think of it as a digital security guard for your remote connections.
Now, before we get too far, let me clarify something: this isn’t meant to scare you off from using VNC altogether. It’s all about being informed and taking the right steps to safeguard your setup. So, whether you’re a business owner, an IT pro, or just someone who loves tinkering with tech, this guide is for you. Let’s jump in and learn how to make your VNC experience as secure as possible.
Read also:Hdhub4u Apk The Ultimate Guide To Downloading And Using The App
Understanding VNC: What Is It Really?
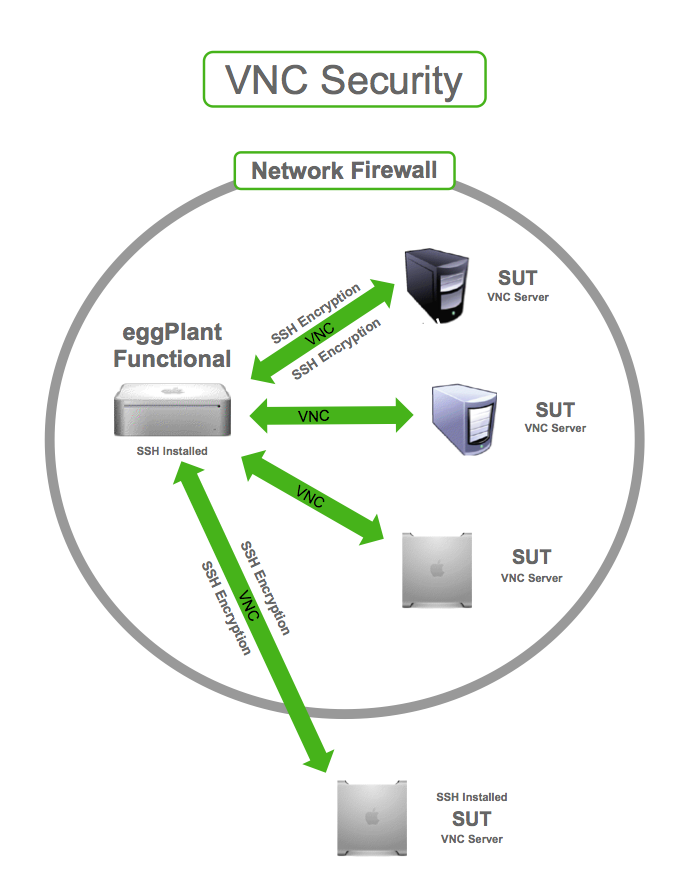
Alright, let’s start with the basics. VNC stands for Virtual Network Computing, and it’s basically software that lets you remotely control another computer over a network. Imagine being able to fix your mom’s computer from across the country or accessing files on your office PC while you’re working from home. Sounds pretty cool, right? But here’s the kicker: VNC works by sending screen updates and keystrokes back and forth, which means there’s a lot of sensitive data flying around.
Key takeaway: VNC is powerful, but it’s only as secure as you make it. Without the right precautions, your remote connection could become a goldmine for hackers.
How Does VNC Work?
Here’s a quick breakdown of how VNC operates. When you connect to a remote computer, VNC establishes a connection between the client (your device) and the server (the remote computer). The server sends screen updates to the client, and the client sends input data like mouse movements and keyboard inputs back to the server. Simple enough, right? Well, not so fast. This constant exchange of data is where things can get dicey if security isn’t a priority.
- VNC uses the RFB (Remote Framebuffer) protocol to transmit data.
- Data is sent in real-time, making it vulnerable to interception.
- Without encryption, anyone on the network could potentially snoop on your activities.
VNC Security Risks: The Dark Side of Remote Access
Now that we’ve covered the basics, let’s talk about the elephant in the room: VNC security risks. These aren’t just hypothetical threats—they’re real problems that have affected countless users worldwide. From unauthorized access to data breaches, the dangers of VNC misuse are significant. Here’s a closer look at some of the most common risks:
Unencrypted Connections
One of the biggest issues with VNC is the lack of default encryption. If your connection isn’t encrypted, anyone on the same network could intercept your data. Think about it: would you walk around with your wallet open for everyone to see? Probably not. Yet, that’s essentially what you’re doing if you use VNC without encryption.
Weak Passwords
Let’s face it—most of us are guilty of using weak passwords at some point. But when it comes to VNC, a weak password is like leaving the keys to your house under the doormat. Hackers love nothing more than guessing simple passwords like “12345” or “password.” If they succeed, they gain full control over your remote system.
Read also:Wwwhdhub4u Movies Your Ultimate Hub For Latest Blockbusters And Classic Cinema
Unauthorized Access
Even if you have strong passwords and encryption, there’s still the risk of unauthorized access. This can happen through brute-force attacks, where hackers repeatedly try different passwords until they find the right one. Or, worse yet, through malware that logs your keystrokes and sends them back to the attacker.
Why Are VNC Security Risks So Important?
Here’s the thing: in today’s digital age, cybersecurity isn’t optional—it’s essential. Whether you’re running a small business or managing a massive enterprise, the last thing you want is for your sensitive data to fall into the wrong hands. VNC security risks are especially critical because they often involve remote access to critical systems. If a hacker gains control of your server, they could wreak havoc on your entire network.
Did you know? According to a recent study, over 60% of data breaches involve some form of unauthorized remote access. That’s why it’s crucial to take VNC security seriously and implement the right safeguards.
The Impact of VNC Security Breaches
Let’s talk numbers for a second. A single VNC security breach can cost a business thousands—or even millions—of dollars in damages. Beyond the financial impact, there’s also the reputational damage to consider. If your customers or clients find out their data was compromised, it could destroy their trust in your brand. Not to mention the potential legal ramifications if sensitive information falls into the wrong hands.
Top 5 VNC Security Tips
Don’t worry—I’m not here just to scare you. There are plenty of ways to mitigate VNC security risks and protect your data. Here are my top five tips for staying safe:
1. Use Strong Passwords
This one’s a no-brainer, but it’s worth repeating. Always use strong, unique passwords for your VNC connections. Avoid common phrases or patterns, and consider using a password manager to generate and store complex passwords securely.
2. Enable Encryption
Encryption is your best defense against data interception. Make sure your VNC software supports encryption protocols like TLS or SSH, and enable them whenever possible. This will ensure that your data remains secure during transmission.
3. Limit Access
Not everyone needs access to your remote systems. Restrict VNC access to only those who absolutely need it, and consider implementing role-based access controls to further limit permissions.
4. Keep Software Updated
Software updates aren’t just annoying pop-ups—they’re essential for patching security vulnerabilities. Make sure you’re running the latest version of your VNC software and any associated tools.
5. Monitor Activity
Regularly review your VNC logs to detect any suspicious activity. If you notice unauthorized access attempts or unusual behavior, take immediate action to secure your system.
Advanced VNC Security Measures
For those of you who want to go the extra mile, here are some advanced security measures to consider:
Firewall Configuration
Configuring your firewall to only allow VNC connections from trusted IP addresses can significantly reduce the risk of unauthorized access. This way, even if someone tries to brute-force their way in, they won’t be able to connect unless they’re on an approved network.
Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring users to provide two forms of identification before accessing a system. This could be something like a password and a one-time code sent to your phone. While not all VNC software supports 2FA natively, you can often integrate it using third-party tools.
Network Segmentation
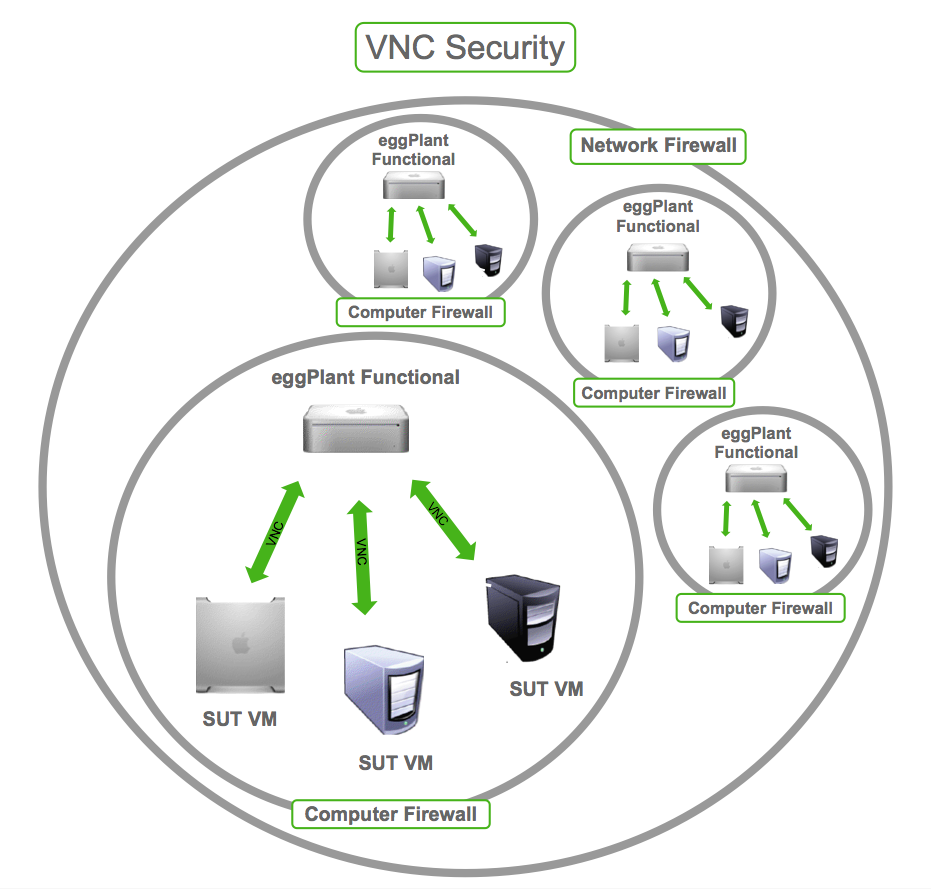
Segmenting your network can help contain any potential breaches. By isolating your VNC servers from the rest of your network, you reduce the risk of a hacker gaining access to your entire system in the event of a breach.
Real-World Examples of VNC Security Breaches
To give you a better understanding of the dangers, let’s look at a few real-world examples of VNC security breaches:
Case Study 1: The Target Breach
In 2013, Target suffered one of the largest data breaches in history, compromising the personal information of over 40 million customers. How did it happen? Through unauthorized VNC access. A hacker gained control of a third-party vendor’s system, which had VNC installed, and used it as a gateway to Target’s network.
Case Study 2: The WannaCry Ransomware
The WannaCry ransomware attack in 2017 infected hundreds of thousands of computers worldwide. One of the ways it spread was through unsecured VNC connections. By exploiting vulnerabilities in outdated software, the attackers were able to gain access to systems and deploy the ransomware.
Conclusion: Stay Safe, Stay Secure
And there you have it—a comprehensive guide to VNC security risks and how to protect yourself. While VNC is an incredibly useful tool, it’s important to remember that with great power comes great responsibility. By following the tips and best practices outlined in this article, you can significantly reduce the risk of a security breach and keep your data safe.
So, what’s next? Take a few minutes to review your VNC setup and make sure everything is secure. Update your passwords, enable encryption, and monitor your logs regularly. And don’t forget to share this article with your friends and colleagues—it could save them from a potential headache down the road.
Remember: cybersecurity isn’t just about technology—it’s about being proactive and staying informed. Stay safe out there, and happy computing!
Table of Contents
- VNC Security Risks: How Safe Is Your Remote Connection?
- Understanding VNC: What Is It Really?
- How Does VNC Work?
- VNC Security Risks: The Dark Side of Remote Access
- Unencrypted Connections
- Weak Passwords
- Unauthorized Access
- Why Are VNC Security Risks So Important?
- The Impact of VNC Security Breaches
- Top 5 VNC Security Tips
- Use Strong Passwords
- Enable Encryption
- Limit Access
- Keep Software Updated
- Monitor Activity
- Advanced VNC Security Measures
- Firewall Configuration
- Two-Factor Authentication
- Network Segmentation
- Real-World Examples of VNC Security Breaches
- Case Study 1: The Target Breach
- Case Study 2: The WannaCry Ransomware
- Conclusion: Stay Safe, Stay Secure