Windows VNC Security Types: A Comprehensive Guide For Safe Remote Access
When it comes to remote access, Windows VNC security types are the backbone of ensuring your data stays protected while allowing seamless connectivity. In today's digital landscape, remote work has become the norm, and with it comes the need for secure methods to access systems from afar. VNC (Virtual Network Computing) is one of the most popular tools for this purpose, but understanding its security protocols is crucial to avoid potential vulnerabilities.
Picture this: You're sitting in a coffee shop, sipping your favorite latte, and you need to access your office PC to retrieve an important document. Sounds easy, right? Well, not exactly. Without proper security measures, you could inadvertently expose sensitive data to malicious actors. That's where VNC security types come into play, offering various encryption methods to keep your connection safe.
Whether you're a tech enthusiast or a casual user, understanding the different types of Windows VNC security is essential. This guide will walk you through everything you need to know, from basic encryption to advanced security protocols, ensuring you're well-equipped to protect your remote connections.
Read also:Movie Rulz Adult The Ultimate Guide To Exploring Highquality Entertainment
What Are Windows VNC Security Types?
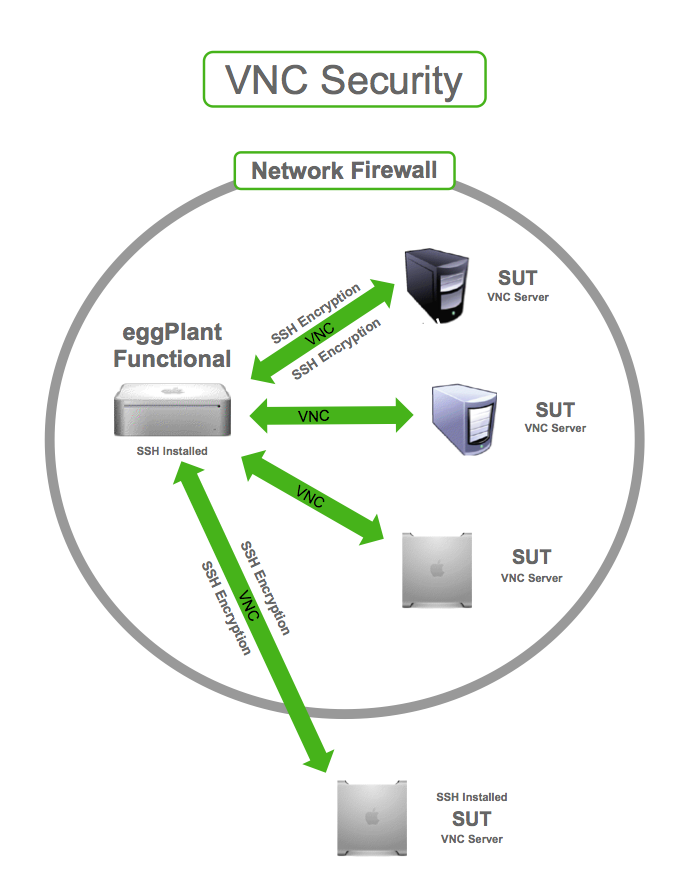
Windows VNC security types refer to the various encryption and authentication mechanisms used to secure remote connections via VNC. These security protocols are designed to prevent unauthorized access and protect sensitive data during transmission. Let's dive deeper into what makes these security types so important:
First off, VNC works by allowing one computer to control another remotely. While this is incredibly useful, it also opens the door to potential security risks if not properly secured. Think of it like leaving your front door unlocked—anyone could walk in without your permission. That's why having robust security measures in place is critical.
Now, let's take a look at some of the most common security types used in Windows VNC:
- None: This is the least secure option, offering no encryption or authentication. It's not recommended for anything other than testing purposes.
- VNC Authentication: This method uses a password to authenticate users but doesn't encrypt the connection, leaving it vulnerable to interception.
- Unix Login: This type of authentication requires users to log in with their Unix credentials, adding an extra layer of security.
Why Security Matters in Remote Access
In the world of remote work, security isn't just a nice-to-have—it's a must-have. With cyber threats becoming increasingly sophisticated, ensuring your VNC connections are secure is more important than ever. Imagine losing access to your business data because of a simple oversight in security settings. Sounds terrifying, right?
By implementing strong security measures, you can:
- Protect sensitive information from unauthorized access.
- Prevent data breaches that could harm your business reputation.
- Ensure compliance with industry regulations and standards.
Remember, even the smallest vulnerability can be exploited by cybercriminals. That's why it's crucial to choose the right security type for your VNC setup.
Read also:Vegamovies Hindi Your Ultimate Destination For Hindi Movies
Common Security Threats in VNC Connections
Before we dive into the different security types, let's first understand the common threats associated with VNC connections. By knowing what to look out for, you can better protect your systems:
- Man-in-the-Middle (MitM) Attacks: Attackers intercept and potentially alter communication between two systems.
- Password Guessing: Weak or easily guessable passwords can lead to unauthorized access.
- Data Interception: Without encryption, data transmitted between systems can be intercepted and read by third parties.
These threats highlight the importance of choosing the right security type for your VNC setup. Let's explore the options in more detail.
Understanding VNC Encryption Protocols
Encryption is one of the key components of VNC security. It ensures that data transmitted between systems is scrambled, making it unreadable to anyone who intercepts it. There are several encryption protocols used in VNC, each with its own strengths and weaknesses:
128-bit AES Encryption: This is one of the most secure encryption methods available. It uses a 128-bit key to encrypt data, making it extremely difficult for attackers to break. Most modern VNC clients and servers support this level of encryption.
SSL/TLS Encryption: Another widely used encryption protocol, SSL/TLS provides secure communication over a network. It's commonly used in web browsers and is also supported by many VNC applications.
DES Encryption: While still used in some older systems, DES encryption is considered less secure compared to modern standards. It's generally recommended to use stronger encryption methods whenever possible.
Choosing the Right Encryption Protocol
When selecting an encryption protocol for your VNC setup, consider the following factors:
- Security Requirements: Determine the level of security needed based on the sensitivity of the data being transmitted.
- Performance Impact: Some encryption methods may slow down your connection speed, so choose one that balances security and performance.
- Compatibility: Ensure that the encryption protocol you choose is supported by both the VNC client and server.
By carefully evaluating these factors, you can choose the encryption protocol that best suits your needs.
Authentication Methods for VNC Connections
Authentication is another critical aspect of VNC security. It ensures that only authorized users can access the remote system. Here are some of the most common authentication methods used in VNC:
Password Authentication: This is the simplest form of authentication, requiring users to enter a password to gain access. While easy to implement, it's important to use strong, complex passwords to enhance security.
Two-Factor Authentication (2FA): This adds an extra layer of security by requiring users to provide two forms of identification, such as a password and a one-time code sent to their mobile device.
Certificate-Based Authentication: This method uses digital certificates to verify the identity of users and systems. It's more secure than password-based authentication but requires more setup and maintenance.
Best Practices for Authentication
To ensure your VNC connections are as secure as possible, follow these best practices:
- Use strong, unique passwords for each VNC connection.
- Enable two-factor authentication whenever possible.
- Regularly update and rotate passwords to prevent unauthorized access.
Implementing these practices can significantly reduce the risk of unauthorized access to your systems.
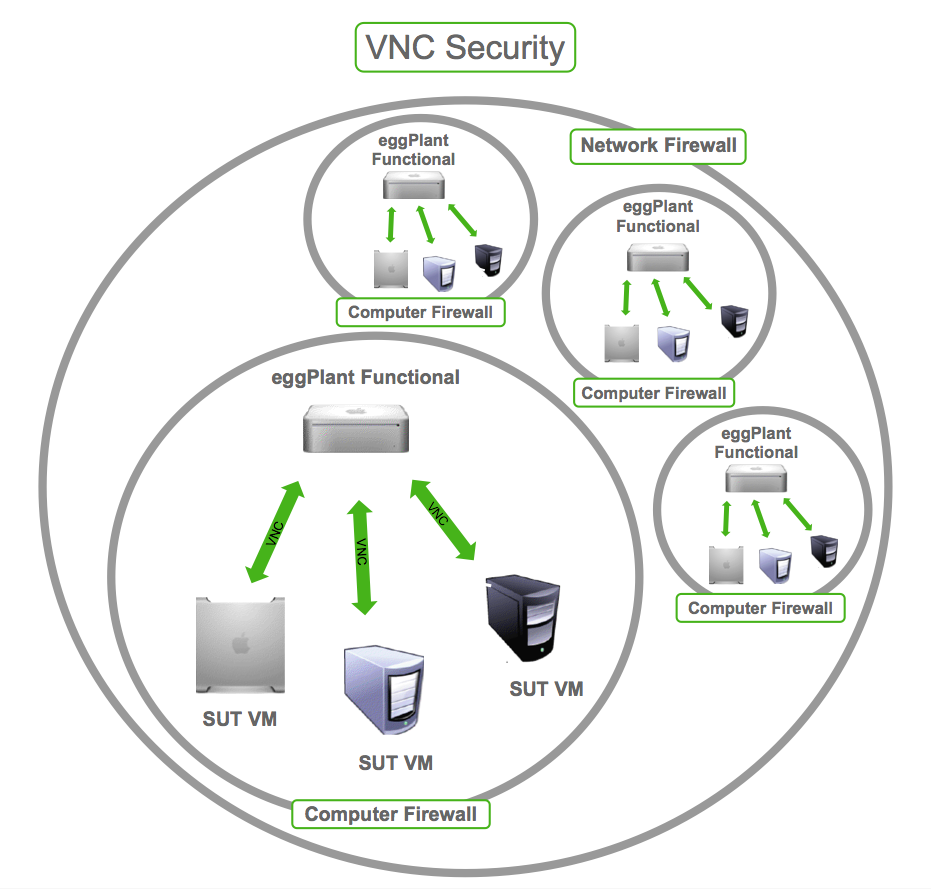
Advanced Security Features in VNC
In addition to encryption and authentication, many VNC applications offer advanced security features to further enhance protection. These features include:
Firewall Integration: Configuring your firewall to allow only specific IP addresses to connect to your VNC server can add an extra layer of security.
Connection Logging: Keeping logs of all VNC connections can help you monitor for suspicious activity and identify potential security breaches.
Session Timeout: Setting a timeout period for idle VNC sessions can prevent unauthorized access if a user forgets to log out.
Implementing Advanced Security Features
To take advantage of these advanced security features, follow these steps:
- Configure your firewall settings to allow only trusted IP addresses.
- Enable connection logging in your VNC application to track all activity.
- Set a reasonable session timeout period to automatically log out idle users.
By implementing these features, you can further safeguard your VNC connections.
Best VNC Clients for Secure Connections
Not all VNC clients are created equal when it comes to security. Some offer more robust features than others. Here are a few of the best VNC clients known for their strong security:
TightVNC: Known for its speed and efficiency, TightVNC offers solid security features, including encryption and authentication options.
RealVNC: This popular VNC client provides enterprise-level security, including SSL/TLS encryption and two-factor authentication.
UltraVNC: Offering a range of security features, UltraVNC is a reliable choice for secure remote connections.
Choosing the Right VNC Client
When selecting a VNC client, consider the following:
- Security Features: Ensure the client offers the encryption and authentication methods you need.
- User Interface: Choose a client with an intuitive interface for ease of use.
- Compatibility: Make sure the client is compatible with your operating system and other software.
Finding the right VNC client can make a big difference in the security of your remote connections.
Windows VNC Security Types in Action
Now that we've covered the basics of VNC security, let's look at how these security types work in practice. Imagine you're setting up a VNC connection between your home computer and your office PC. Here's how you might configure the security settings:
Step 1: Choose an encryption protocol, such as 128-bit AES encryption, to secure the data transmitted between the two systems.
Step 2: Set up authentication using a strong password and enable two-factor authentication for added security.
Step 3: Configure your firewall to allow only your home IP address to connect to the VNC server on your office PC.
By following these steps, you can establish a secure VNC connection that protects your data from potential threats.
Troubleshooting Common Security Issues
Even with the best security measures in place, issues can arise. Here are some common problems and how to resolve them:
- Connection Refused: Check your firewall settings to ensure the VNC port is open and allowed.
- Authentication Failed: Double-check your password and ensure two-factor authentication is properly configured.
- Data Not Encrypted: Verify that the encryption protocol is correctly set up on both the client and server.
Addressing these issues promptly can help maintain the security of your VNC connections.
Conclusion: Protecting Your Remote Connections
In conclusion, understanding and implementing the right Windows VNC security types is essential for protecting your remote connections. By choosing the appropriate encryption protocols, authentication methods, and advanced security features, you can ensure your data remains safe from potential threats.
We encourage you to take action by reviewing your current VNC setup and making any necessary adjustments to enhance security. Don't forget to leave a comment below sharing your thoughts or experiences with VNC security. And if you found this guide helpful, feel free to share it with others who might benefit from the information.
Stay safe, stay secure, and happy remote working!
Table of Contents
- What Are Windows VNC Security Types?
- Why Security Matters in Remote Access
- Understanding VNC Encryption Protocols
- Authentication Methods for VNC Connections
- Advanced Security Features in VNC
- Best VNC Clients for Secure Connections
- Windows VNC Security Types in Action
- Troubleshooting Common Security Issues
- Conclusion